$18 million of fraudulent charges from the app blocked by malware security platform Secure-D
London, October 31st, 2019 – A popular Android keyboard app, ai.type, downloaded more than 40 million times and included in the Google Play app store, has been caught making millions of unauthorized purchases of premium digital content, researchers at mobile technology company Upstream report. The app has been delivering millions of invisible ads and fake clicks, while delivering genuine user data about real views, clicks and purchases to ad networks. Ai.type carries out some of its activity hiding under other identities[1], including disguising itself to spoof popular apps such as Soundcloud. The app’s tricks have also included a spike in suspicious activity once removed from the Google Play store.
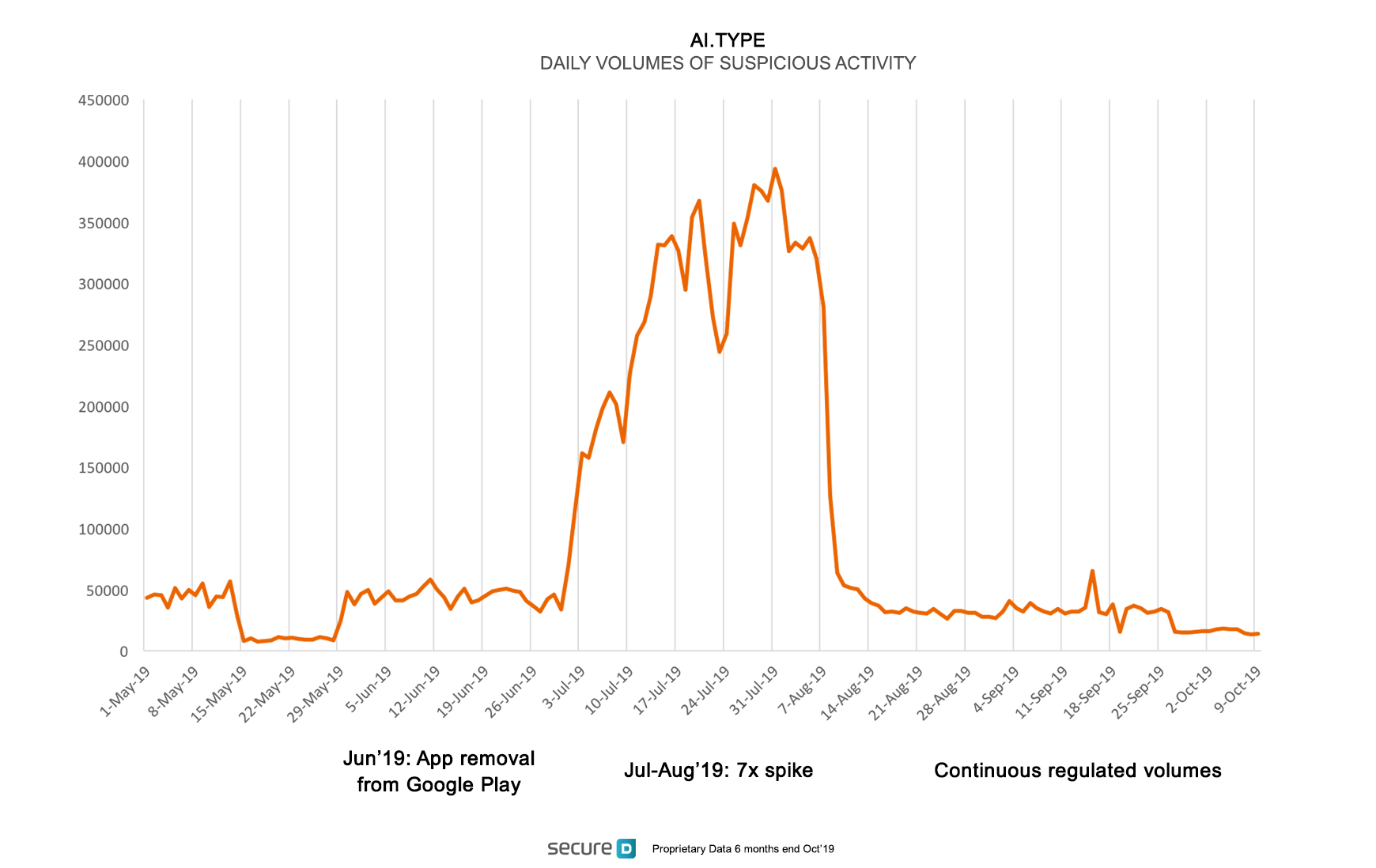
The Upstream Secure-D mobile security platform has so far detected and blocked more than 14 million suspicious transaction requests from only 110,000 unique devices that downloaded the ai.type keyboard. If not blocked these transaction requests would have triggered the purchase of premium digital services, potentially costing users up to $18 million in unwanted charges. The suspicious activity has been recorded across 13 countries but was particularly high in Egypt and Brazil.
Ai.type is disguised as a free treat for mobile users. It is a customizable on-screen keyboard app developed by Israeli firm ai.type LTD, which describes the app as a “Free Emoji Keyboard”. Despite the fact that the app was removed from Google Play in June 2019, the app remains on millions of Android devices and is still available from other Android marketplaces. Shortly after the removal from Google Play, in July 2019, suspicious activity spiked exponentially for a two-month period. It has since remained high, though in lower volumes than during the summer spike.
[1] As instructed by a Command & Control Server
Upstream CEO, Guy Krief, commented:“Malware can be responsible for creating millions of dollars of fraudulent mobile advertising revenue. It seriously impacts consumers’ pockets and mobile service experience by eating up their data, incurring unwanted charges, and affecting the performance of their phones.
The mobile advertising fraud market is worth some $40bn annually. In any given market one in ten devices is infected with malware. Dressing up to appear as legitimate and often popular applications, undetected malware damages the industry’s reputation, leaving mobile operators and their customers to pick up the tab.”
Head of Secure-D at Upstream, Dimitris Maniatis, explains more about how the app tricks users: “Ai.type contains software development kits (SDKs) with hardcoded links to ads and subscribes users to premium services without their consent. These SDKs navigate to the ads via a series of redirections and automatically perform clicks to trigger the subscriptions. This is committed in the background so that normal users will not realize it is taking place. In addition, the SDKs obfuscate the relevant links and download additional code from external sources to complicate detection even from sophisticated analysis techniques. Bottom line: innocent users are paying for these hidden, unauthorized purchases and related data consumption whose source is buried in the app.”
Upstream is advising all consumers who have downloaded ai.type to check their phones for unusual behavior. Users should regularly check their phones and remove any reported malware. They should also check their bills for unwanted or unexpected charges for accessing premium data services and to look out for signs of increased data usage which could indicate a malicious app is consuming data in the background.
Upstream works directly with mobile operators to pro-actively safeguard their subscribers against fraud on their mobile devices – and currently protects tens of millions of mobile users worldwide. Its Secure-D anti-fraud platform uses machine learning algorithms to determine the transactions that are most likely to be fraudulent and uses behavioral patterns to detect anomalies and unwanted transaction patterns. In 2018 alone, Upstream processed more than 1.8 billion mobile transactions, identified more than 30 million infected devices, and blocked more than 63,000 malicious apps with Secure-D.
For the full report on the investigation please click here
###
For more information please contact:
Upstream Corporate Communications
Ε: corp.comms@upstreamsystems.com