THE ISSUE IN SUMMARY
An unusually high number of transaction attempts encountered by Secure-D in Brazil and Malaysia coming from a series of Alcatel Android smartphone models Pixi 4 and A3 Max, led our analysts to investigate deeper. In doing so we identified that a pre-installed Weather forecast application, siphons a lot of data and attempts such transactions. The application package is com.tct.weather and comes from TCL Corporation, a Chinese tech firm known for making the Alcatel and Blackberry devices. It collects and transmits geographic locations, email addresses, IMEIs to a server in China and has a number of privacy invasive permissions on the device. The application is also available on the Google Play store and has more than 10m installs with a seemingly healthy 4.4 user rating. Had it not been blocked it would have succeeded to subscribe users on Alcatel phones in countries like Brazil, Malaysia and Nigeria to paid services for which users would have been billed more than $1.5 million. This activity occurred in the background and succeeded in remaining undetected by the users, behaving liek a typical malicious application. These findings further expand on the previously covered case of Gmobi, a provider of Firmware-Over-The-Air technology (FOTA) to mobile device manufacturers that also relied on their pre-installed application to attempt ad fraud and misuse personal information.
WHAT LEAD US TO INVESTIGATE
Over July and August 2018, through Secure-D, we observed a higher than usual number of transaction attempts in Brazil and Malaysia coming from a series of Alcatel Android smartphones (Pixi 4 and A3 Max models). Those suspicious requests were initiated by the same application named com.tct.weather in both Brazil & Malaysia. This com.tct.weather Android application is pre-installed on many Alcatel devices and is also available for download on Google Play. It provides “accurate forecasts and timely local weather alerts”. It has been downloaded by more than 10,000,000 users from Google Play. Similar transaction attempts coming from Alcatel devices and the application com.tct.weather were also blocked in Nigeria, South Africa, Egypt, Kuwait and Tunisia.
SETTING UP THE INVESTIGATION
We launched a process to purchase multiple devices from their owners with the purpose of investigating them in our lab. One of those – an Alcatel A3 Max – being from a user whose device had initiated more than 500 transaction requests over the months of July and August. It is worth mentioning that the vast majority of users we contacted verified they were experiencing their phone was “acting up”. Most complained about unwanted charges and their device/ battery overheating (from CPU overuse). In our lab, the devices were placed in a “sandbox” environment where all network traffic (data transmitted from and to the device) is recorded.
HOW THE APPLICATION ATTEMPTS AD-FRAUD, CONSUMES GBs OF DATA AND MISUSES PERSONAL INFORMATION
As soon as the device was placed in the “sandbox”, the com.tct.weather Android application immediately initiated calls to servers that are not related to the application’s main function. The application collects and transfers users’ personal information to servers in China. Based on our observations, the app collects the user’s device ID, email and location having achieved consent via the following way:
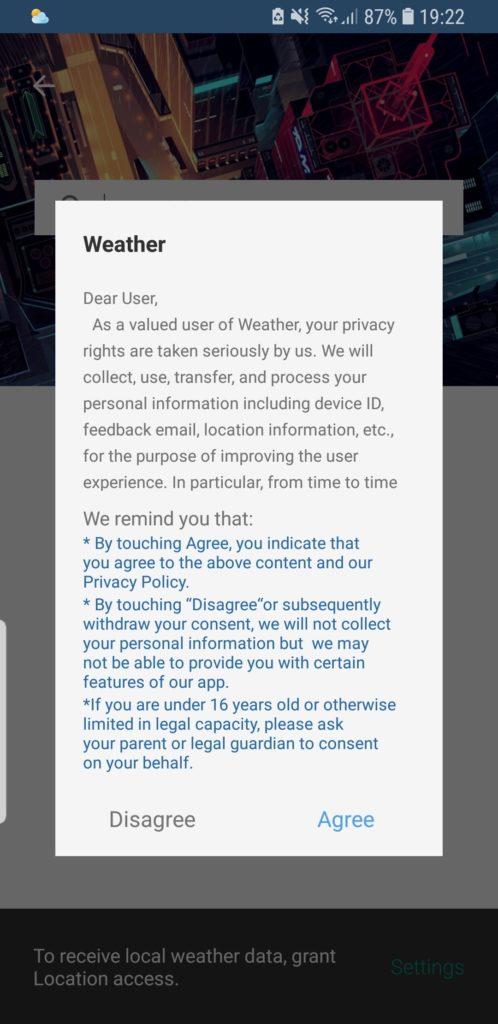
As soon as the device was placed in the “sandbox”, the application also started – in the background (i.e. not visible to the user) – accessing web pages with digital ads. A specific url (https://traffic.tc-clicks.com/?p=6070&media_type=adult&click_id=2-35d4a42fc0e859aac674a67115e9df9e_1536072819&pi=122 of the domain traffic.tc-clicks.com) was being continuously requested by the app, which in turn was redirecting to web pages with digital ads. The application was then clicking the buttons on those pages, without user interaction nor consent.
In the examples below ad-fraud is attempted by loading a page with ads and also programmatically generated clicks triggered the purchase of a paid subscription (the JokerVR service) and consequent charges to the airtime of the user.
Intermediate Page Loaded for Ad-Fraud Purposes
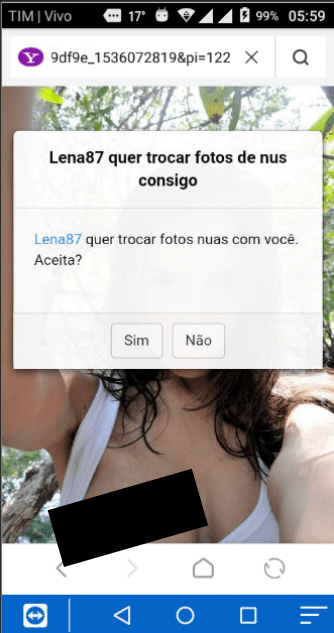
Subscription Service Page

In this 2nd example, the application went through multiple urls eventually redirecting it to the purchase page of a premium digital service available to subscribers of TIM Brazil (one of the largest mobile operators in Brazil). The SIM card on the device under investigation was one of TIM in Brazil.
The application then proceeded with clicking the “Assinar” (subscribe) button and attempted to subscribe the user to the premium service. The same process was applied to the following page where the user should confirm its purchase, with the application clicking on the “Confirmar Assinatura” (confirm subscription) button.
Following the above attempts, the application then proceeded with contacting another server via a url (http://bitetraff.com/l/20464460927af661659e?sub=7ba17456F6ed1U4ef9N813dNd75b29e5e8a6Y1536072859961&source=2382) that again led to web pages with digital ads on which the application performed untriggered programmatic clicks. All this activity, unintended by the user and non visible, consumes important amounts of data. We recorded 50MB to 250MB of data per day being consumed by the application’s unwanted activity.
ANDROID PERMISSION ABUSE
While investigating the application we extracted the pre-installed apk file and analyzed the permissions it has access to, finding them to be misused and providing a seemingly simple Weather forecasting application with excessive permissions able to gather and transmit personal information from the user.
Table of permissions
| Permission | What it allows |
| android.permission.CHANGE_WIFI_STATE | Allows the application to change the state of the wi-fi network. |
| android.permission.MOUNT_UNMOUNT_FILESYSTEMS | Allows mounting and unmounting of file systems (i.e. external SD cards). Android documentation says the permission is NOT intended for 3rd party applications |
| android.permission.READ_PHONE_STATE | Allows read only access to phone state, including the phone number of the device, current cellular network information, the status of any ongoing calls, and a list of anyPhoneAccounts registered on the device. Documentation says that this permission is DANGEROUS |
| android.permission.WRITE_EXTERNAL_STORAGE / android.permission.READ_EXTERNAL_STORAGE | Allows reading and writing of the external storage. This is dangerous (as the application can have access to other user files and/or 3rd party app logs, system logs. This means that the application can read/write everything it wants and the read data might be sent to the server |
| android.permission.ACCESS_KEYGUARD_SECURE_STORAGE | This permission was removed in the OS since 4.4 (KitKat). But for devices that are below that version, this permission is able to control a flaw in the OS to lock and unlock the device at any time (like pressing the power button and unlocking the phone) |
| android.permission.READ_LOGS | Allows an application to read the low-level system log files.
Not for use by third-party applications, because Log entries can contain the user’s private information. |
| android.permission.SET_DEBUG_APP | Configure an application for debugging.
Not for use by third-party applications. |
The pre-installed and the downloadable on Google Play Store version of the com.tct.weather application require different Android permissions (capabilities or information that the application can access).
Google Play downloadable version: it requires special and high risk permissions like the ones below:
‘READ_LOGS’ access: an intrusive access, which according to Google’s Android developers guide allows an application to “read the low-level system log files” and is “Not for use by third-party applications, because Log entries can contain the user’s private information”
SYSTEM_ALERT_WINDOW and WRITE_SETTINGS : according to Google’s Android developers guide, these are permissions that very few applications should use as they are intended for system-level interaction with the user and allow an application to read or write the system settings of the phone. If an app needs one of these permissions, it must declare the permission in the manifest (file with all the essential information about the application to the Android system) and request the user’s authorization. The com.tct.weather application does not ask users for any such authorization.
Pre-installed version: in addition to the permissions required by the downloadable version, the pre-installed application also requires access to:
BILLING which is used for in-app billing, even though the application does not include any Google Play billing functionality.
SIZE OF THE ISSUE
In Brazil, 2.5 million transaction attempts initiated from this Weather application on Alcatel devices were blocked in July and August 2018. Those 2.5 million transaction attempts to purchase a digital service originated from 128,845 unique mobile phone numbers.
In Brazil again but for another premium digital service, 428,291 transaction attempts initiated from this Weather application on Alcatel devices were blocked in July and August 2018.
In Kuwait, 78,940 transactions attempts initiated from Alcatel devices were blocked in July and August 2018. Transaction attempts initiated by this Weather application on Alcatel devices were also blocked in Nigeria, South Africa, Egypt and Tunisia. As for the downloadable version of Weather-Simple weather forecast, available on Google Play Store, it has over 10m downloads globally and has reached #6 in downloads within its category in Google’s UK Play Store.
TCL AND ALCATEL
Alcatel is a French brand of mobile handsets owned by Finnish consumer electronics company Nokia and used under license by Chinese electronics company TCL Corporation. On Google Play Store, the developer of Weather-Simple weather forecast appears under mie-alcatel.support, while TCL Communication Limited appears when looking at the privacy policy of the app. And when looking at the other Android applications offered by the mie-alcatel.support on Google Play Store, we can find the 4 applications below, one of them being called TCL Weather.

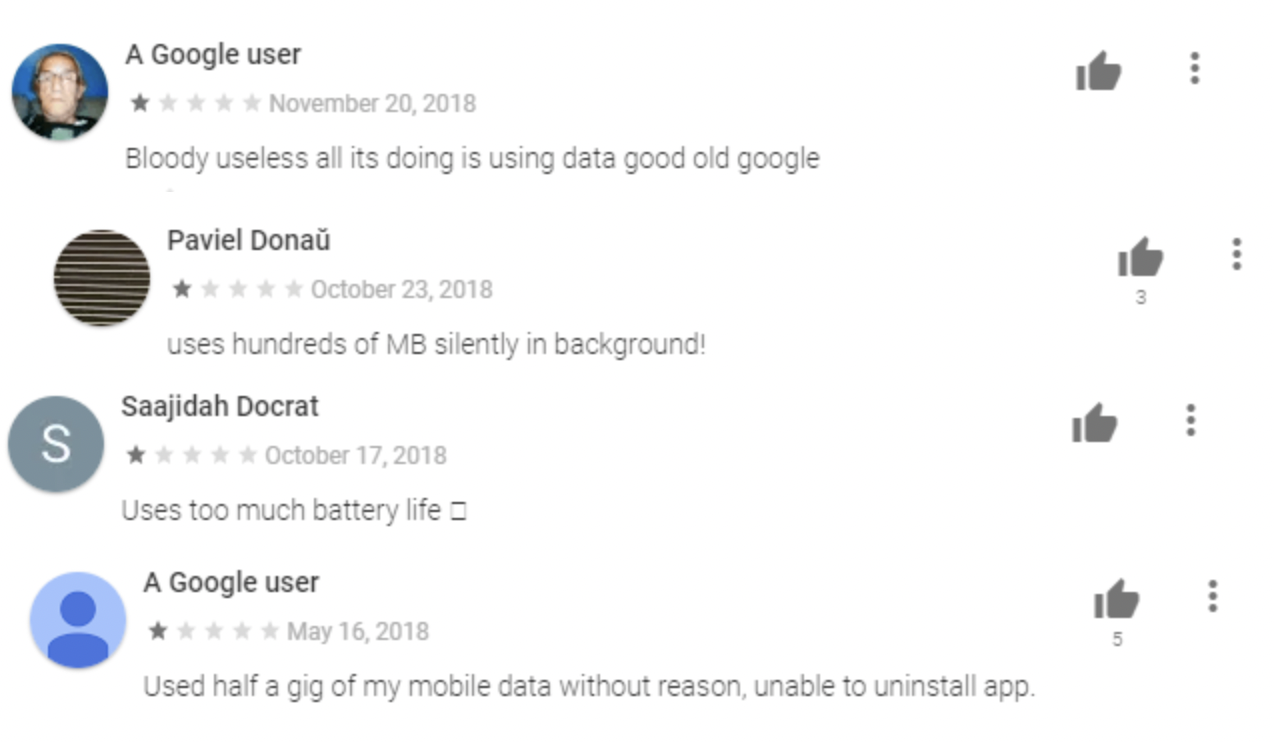
Looking closer at the user ratings of Weather – Simple Weather, reveals a barrage of one or two worded 5 star ratings that succeed in pushing down user complaints that reveal the malicious effects they experience.
CONCLUSION AND EFFECTS ON USERS
Owners of TCL manufactured Alcatel Android smartphones across multiple countries are being affected by the pre-installed application com.tct.weather, resulting in:
- Systematic collection & transfer of their personal information to servers in China.
- Depletion of their data allowance – a major issue in emerging markets where the cost of data is dramatically high. In Brazil, for example, 1GB costs the equivalent of 6h of work on minimum wage (vs. 30 min in Germany).
- Unwanted transactions and charges to their prepaid airtime which is the only way users can pay for digital services in emerging markets.
Tens of millions of Android Smartphone users across the globe are being affected similarly when downloading TCL’s Weather-Simple weather forecast from Google’s official Play Store. Overall, whether pre-installed on Alcatel devices or downloaded from Google’s official Play Store, the application com.tct.weather has generated over 27m transaction attempts across 7 markets. Had they not been blocked by Secure-D these transactions would have translated into $1.5m unwanted charges to users’ airtime.
Update (Saturday, Jan. 5, 8:23pm GMT):
Following the publication of the research findings in The Wall Street Journal, the application has been removed from Google Play.
—
Secure-D combines machine learning algorithms with payment processing workflows to protect mobile operators and their subscribers against online transaction fraud and data depletion, caused by all types of malware and other online threats. The platform processes over 480 million transaction requests per month, has detected and blocked over 42,000 malicious apps and has identified more than 19 million infected smartphones around the globe.
This story is covered by the Wall Street Journal, read it here.

