Upstream’s security lab, Secure-D, has unveiled that 4shared, a popular file sharing and storage Android app hides suspicious background activity. 4shared has been delivering bogus ads to user devices that generate fake views, clicks and purchases; then reports falsified engagement metrics back to advertising networks. The ads are never seen by users and don’t actually appear on screen.
UNVEILING THE INVESTIGATION
Over a recent period, Secure-D, identified and blocked more than 114 million suspicious mobile transactions originating from the same Android app, 4shared. These transactions originated from 2 million unique mobile devices across 17 countries and could have cost users up to $150 million in unwanted charges.
4shared is a popular file sharing and storage mobile and desktop app. Available since 2011 it has received generally positive ratings from sources like PC World, Softonic, and Microsoft Store. The Android app generated over 100 million downloads and ranked second in its category in Austria, 7th in Italy, and 10th in Switzerland. Yet on 17th of April 2019 it was abruptly removed from Google Play – then replaced the following day. The new version has been submitted as an entirely new app – not a version update – but keeps the original 4shared icon, with a “new” ribbon on it. As of June 21st, there have been more than 5 million installs of the ‘new’ 4shared on Google Play, free from the code responsible for the suspicious activity, unlike the more than 100 million previous app users that remained affected. Android users have rated it 4.6 out of 5. 4shared is developed by Ukrainian firm New IT Solutions Ltd.
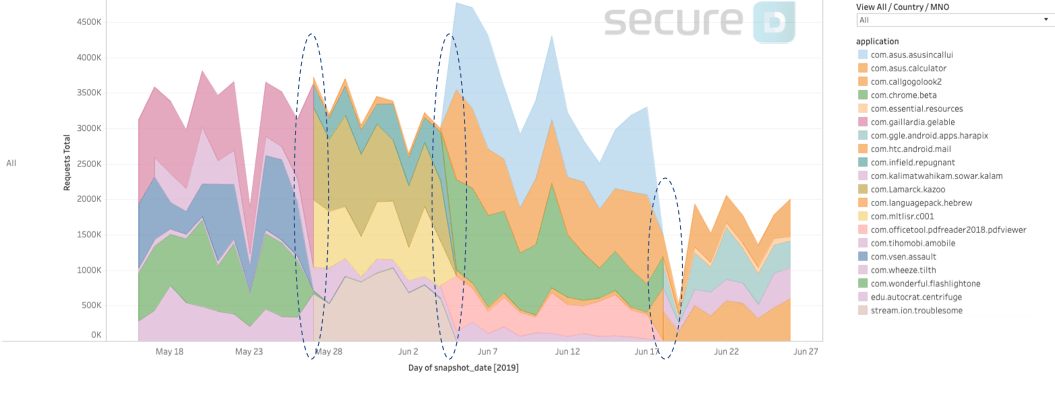
Continuing to monitor the activity of 4shared in June, Secure-D has uncovered that the app is attempting to mask its identity whilst conducting suspicious activity. Instead of appearing under its own name, it assumes the names of either existing legitimate apps (like com.chrome.beta – the new beta version of Google’s Chrome browser) or non-existing ones. The app seems to be using multiple fake names at the same time which it regularly and simultaneously changes (see graph below).
SETTING UP THE INVESTIGATION
Secure-D recorded a high number of suspicious non-user-initiated subscriptions to digital services leading to unwanted airtime charges. We purchased one of the devices, that performed a high number of subscriptions attempts, from its owner and placed it in our lab for investigation. The handset was a SAMSUNG GALAXY J1 MINI PRIME, SM-J106 and had the 4shared app installed. The testing began with a dynamic analysis of the device to detect and record HTTP network traffic in and out of the device.
THE ALARMING FINDINGS: 4SHARED’S SUSPICIOUS BEHAVIOR
During the testing, subscription verification SMSs were sent on the device when an unwanted subscription was attempted, allowing Secure-D experts to isolate and examine the relevant traffic.
Static and Behavioural analysis showed that the 4shared application was communicating with command and control servers, and after multiple redirects would then connect to the purchase portal for premium digital services.
The Secure-D team observed communication taking place and a number of embedded SDKs in the 4shared application were involved. The SDKs were as follows:
– com.elephant.data
– com.elephantdata
– com.unit.two
– com.unit.three
On further analysis the SDKs were found to contain obfuscated hardcoded URLs, creating the redirection chain that led to the unwanted subscriptions.
The obfuscated URLs were:
– kdata.elephantdata.net
– udata.elephantdata.net
– pdata.elephantdata.net
– sdata.elephantdata.net
– sub.zkmobi.com
The embedded SDKs were designed to navigate to a number of advertisement services, and then perform automated ‘clicks’ on the ads. All of this took place invisibly in the background without any user interaction. The flow is described below:
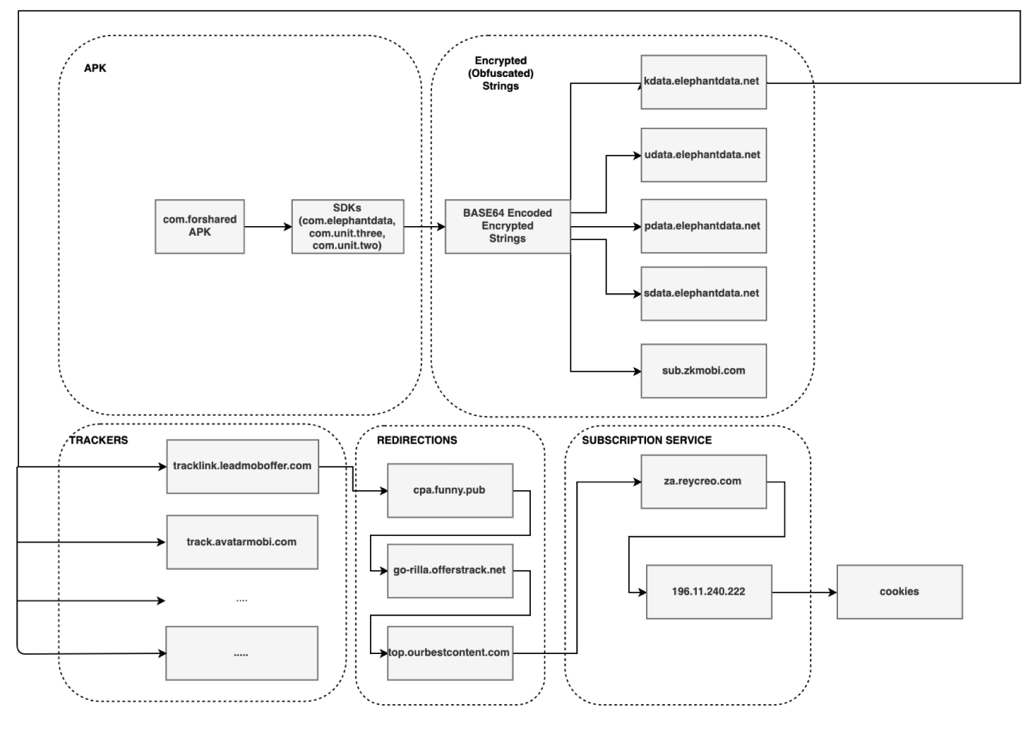
Analysis showed that the initial link for the invisible advertisements’ trackers had been obfuscated, while the message containing the location URL of the dynamically provided code is transferred encrypted – a non-standard setup suggesting that the intent of the SDKs was suspicious.
The in-depth analysis also recorded the path of redirections, leading to a fraudulent ad click, and an unwanted subscription to a premium digital service:
1. http://tracklink.leadmoboffer.com/
2. http://cpa.funny.pub/
3. http://go-rilla.offerstrack.net/
4. https://top.ourbestcontent.com/
5. http://za.reycreo.com/
6. http://196.11.240.222/
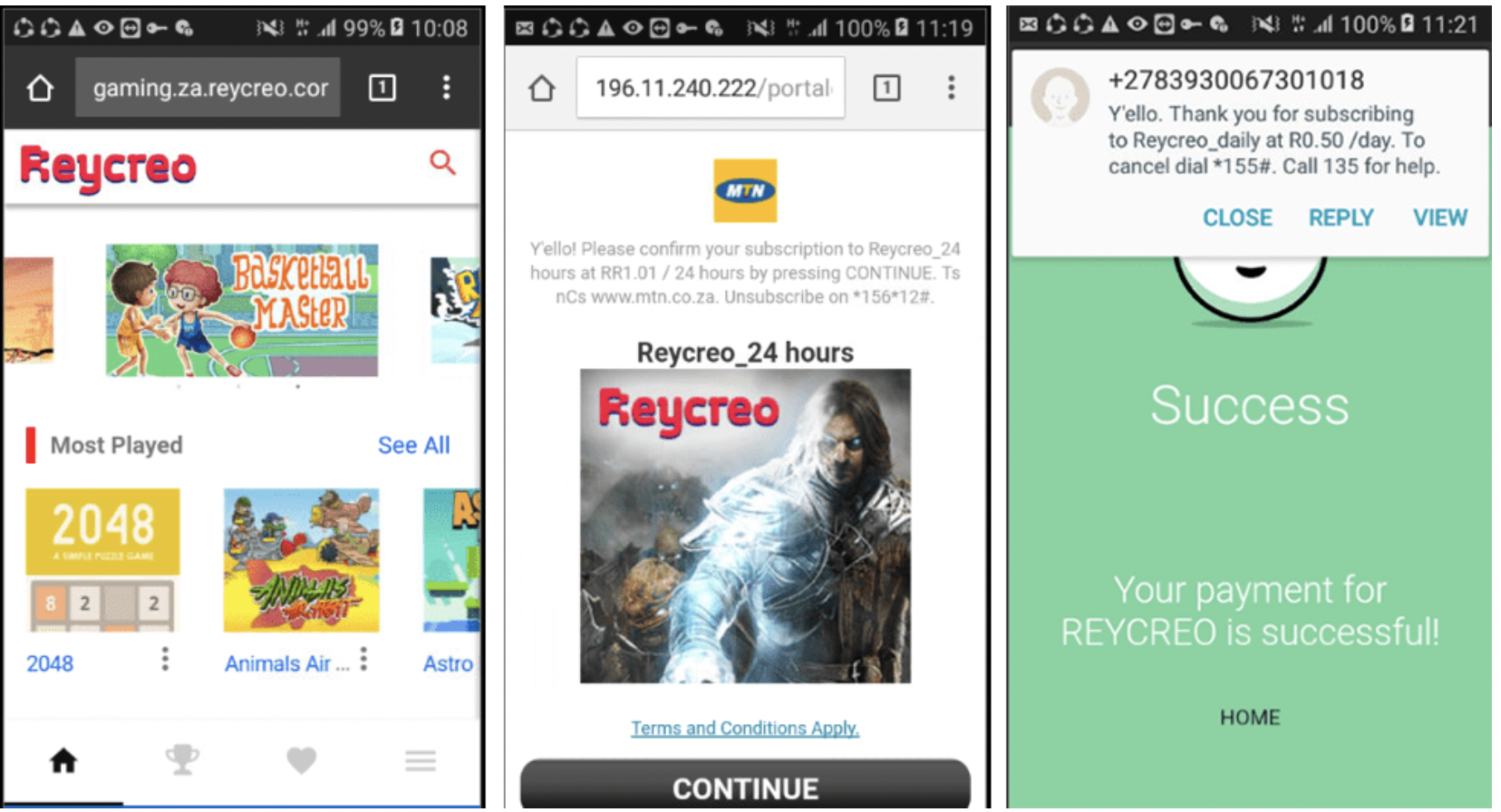
Examples of landing pages loaded by the app in the background and completely invisible to the user:
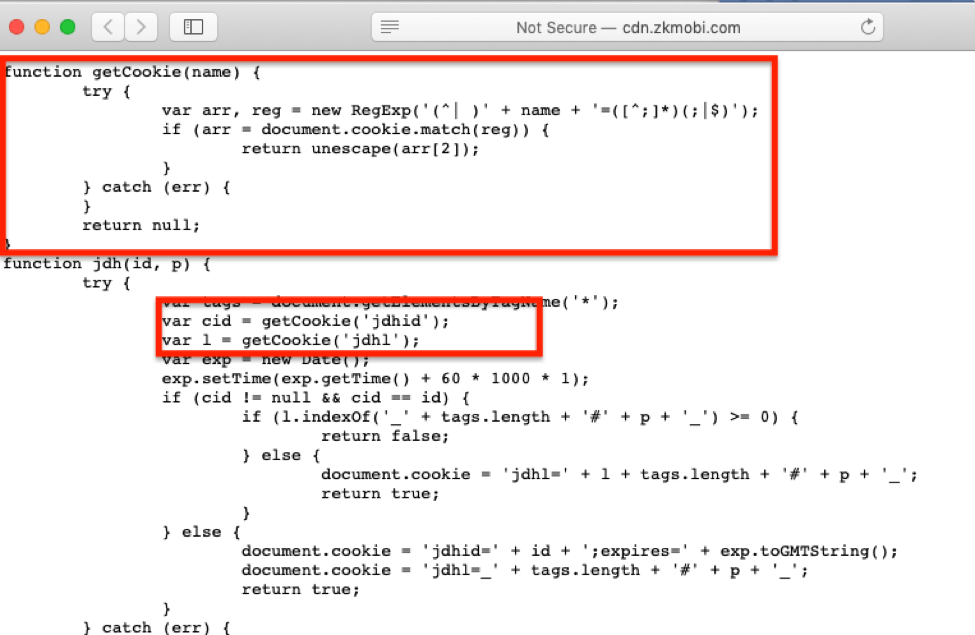
The SDK also downloaded a JavaScript file which executed the automated clicks. It also set cookies in order to determine whether a “click” had already been made for a specific ad in the past. The code below shows the cookie parsing capability of the JavaScript file for cookies relevant to the subscription service:
The URL for the JavaScript file was obtained through a compressed and encrypted server response from the “kdata.elephantdata.net” server, and then loaded through the SDK “com.unit.two”.
The links that enabled the redirections to the subscription service, and the link to the JavaScript file that performs the automated clicks, were all hosted on completely different servers – a clear indication that a domain-fronting technique was being used to cloak the fraudster’s identity.
The application was also transmitting personal data, including deviceType, deviceId, userId, deviceCategory, sessions, activeDays, lastSession, AgeMin, AgeMax, and Gender to servers located in the British Virgin Islands and the United States. This operation is enabled with user consent. According to Google Play Privacy Statement, 4share users have the option to consent or not to the collection and use of their personal information.
In addition, the analysis showed that 4shared for Android uses intrusive permissions that are unrelated to its stated functions. The following are classified as dangerous:
| Permission | What it allows |
| android.permission.ACCESS_FINE_LOCATION android.permission.ACCESS_COARSE_LOCATION |
Allows the application to access the user’s location. |
| android.permission.READ_PHONE_STATE | Allows the application to read device/phone data including the phone number of the device, current cellular network information, the status of any ongoing calls, and a list of any phone accounts registered on the device. |
| android.permission.READ_CONTACTS | Allows the application to read user’s contacts’ data. |
| android.permission.READ_EXTERNAL_STORAGE android.permission.WRITE_EXTERNAL_STORAGE |
Allows the application to read or write to the phone’s external storage. |
| android.permission.GET_ACCOUNTS | Allows access to the list of existing accounts on the device. |
| android.hardware.CAMERA | Allows access to the camera device. |
SCALE OF THE ISSUE & IMPACT
Secure-D blocked more than 114 million suspicious mobile transactions initiated by 4shared across 2 million unique devices. The 114 million mobile transaction alone could have totaled up to $150 million USD in airtime charges. In many emerging markets, debits against pre-paid airtime are the only way users can access digital and mobile broadband services.
Most of the suspicious mobile transactions – which are still on-going – coming from devices in Brazil (110 million suspicious attempts), Indonesia and Malaysia. Secure-D has also seen fraudulent mobile transaction’s activity from 4shared in another 14 countries.
CONCLUSIONS, EFFECTS ON USERS
4shared was being used fraudulently to fake user engagement metrics and claim revenue from online advertising networks resulting in major consequences for the end users:
- Unwanted and unexpected airtime charges for premium digital services without user consent.
- Unexpected depletion of their data allowance and reduced battery life, even when the device is not in use, due to the unseen background activity.
- Transfer of users’ personal information to servers located in the British Virgin Islands and the US. This personal user data may include deviceType, deviceId, userId, deviceCategory, sessions, activeDays, lastSession, AgeMin, AgeMax, and Gender.
Mobile ad fraud is growing in frequency and sophistication. To avoid falling victim to mobile ad fraud, Android users should immediately check their phones to see if they have any suspicious app installed. If so, they should uninstall it immediately and review any recent mobile airtime charges for possible fraud. In most cases, only installing Android apps from Google Play is a good rule of thumb – but even apps from legitimate sources can be compromised. Before any installation users should check the app’s reviews, developer details, and list of requested permissions, making sure that they all relate to the app’s stated purpose.
FOR MOBILE NETWORK OPERATORS, CONTENT PROVIDERS & AGGREGATORS, CLIENTS OF SECURE-D
Secure-D has been blocking all suspicious activity by 4shared since its onset.
FOR INFORMATION SECURITY EXPERTS
Secure-D shares its findings with the community to help combat fraud and eliminate online threats. To request the infected 4shared APK, the complete technical analysis, a list of infected apps, security professionals can contact info@secure-d.io
Secure-D has worked with TechCrunch to bring this story to light. You can read their write up here.
Update: Following the publication of Secure-D report, 4shared reached out stating that they were not aware of the background activity of the app, and that they had removed the Elephant Data SDK in the new release of the application. Users of older versions which still contain the SDK should update to the newest version manually.

